Cybercrime refers to criminal activities committed through the Internet or other forms of digital communication technology. Identity theft, fraud, online harassment, and malware distribution are all examples of these crimes. To carry out their actions, cybercriminals may employ a range of methods, including breaking into computer systems, phishing assaults, and the deployment of botnets to enable distributed denial of service (DDoS) attacks. Cybercrime is rapidly evolving, and keeping track of the latest trends and developments can be challenging. This article will explore the top 20 trends in cybercrime in the present world. Cybercrime is a significant and evolving threat in the present world. From ransomware attacks to the use of artificial intelligence in cybercrime, the tactics and techniques used by cybercriminals are constantly evolving. Individuals and organizations need to stay vigilant and take steps to protect themselves against these threats.

1. Ransomware Attacks Continue To Rise
Ransomware is a form of harmful malware that encrypts the victim’s files. The hackers then demand a ransom from the targeted victim to restore access to the data upon payment. These attacks have been on the rise in recent years and can have devastating consequences for individuals and organizations. Ransomware attacks are especially damaging to businesses because they disrupt critical business processes and result in significant financial losses. The attackers may threaten to publish the victim’s data or expose sensitive information if the ransom is not paid.

2. Phishing Attacks Have Become More Sophisticated
Phishing attacks are a common type of cybercrime in which attackers send fake emails or texts that are visible to be from legitimate sources to trick the targeted victim into revealing sensitive information, such as passwords or financial information. These attacks are becoming more sophisticated, and attackers use increasingly convincing tactics to lure victims in. Phishing attacks are especially effective because they frequently use personalized messages or seemingly legitimate requests to trick victims into disclosing sensitive information. An attacker, for example, could send an email purporting to be from a bank or other financial institution, requesting that the recipient log in to their account to verify their personal information. If the victim falls for the ruse and enters their login credentials on the bogus website, the cyber attacker will be able to access the victim’s account.

3. Increase In Attacks On Healthcare Organizations
Healthcare organizations have become prime targets for cybercriminals due to the comparatively sensitive nature of the information they hold. In past years, there has been a significant increase in attacks on healthcare organizations, including data breaches and ransomware attacks. Because of the throughout sensitive nature of the data they handle and the potential for attackers to profit from stealing and selling this data on the black market, healthcare organizations are a common target for cyber attacks.

4. Cryptocurrency-Related Crimes On The Rise
With the growing popularity of cryptocurrencies, it’s not surprising that cybercriminals are increasingly targeting these digital assets. This includes attacks on cryptocurrency exchanges, scams, and fraud involving cryptocurrencies. Cryptocurrencies are digital or virtual currencies that employ encryption to safeguard financial transactions. Like any other financial asset, cryptocurrency can be used for legitimate and criminal purposes.

5. Internet Of Things (Iot) Devices Has Become A Target
The proliferation of IoT devices has created new opportunities for cybercriminals. These devices are poorly secured and can provide an easy entry point for attackers. Malware infection is a common type of IoT attack in which malicious software is installed on a device, allowing the attacker to gain control or use it to launch additional attacks. Unauthorized access to a device is another common type of IoT attack in which the attacker gains access to a device by exploiting vulnerabilities or using weak passwords.

6. Increasing Use Of Artificial Intelligence In Cybercrime
Cybercriminals use artificial intelligence (AI) and machine learning to automate and scale attacks. This includes using AI to generate convincing phishing emails and developing malware that can evade detection by traditional security systems.AI can be used to automate the process of carrying out cyberattacks, such as creating and sending phishing emails or identifying and exploiting system vulnerabilities. We can also use AI to analyze and interpret large amounts of data to detect patterns or anomalies that may indicate a cyber attack is taking place.

7. State-Sponsored Cyberattacks On The Rise
Governments worldwide are increasingly using cyberattacks as a tool for espionage and sabotage. These state-sponsored attacks can be highly sophisticated and often target critical infrastructure and government agencies. Governments or state-sponsored organizations carry out these attacks with the intent of gathering intelligence, disrupting systems, or causing damage to a target. They can be extremely sophisticated, making detection and defense difficult. State-sponsored attackers may employ a variety of tactics, including phishing attacks, malware infections, and exploits of software or hardware vulnerabilities.
8. Chain Attacks Have Become More Common
Supply chain attacks involve compromising a third-party vendor or supplier to gain access to a larger organization. These attacks have become more common in recent years, as they can be an effective way for cybercriminals to access a target’s systems. Supply chain attacks are a type of cyberattack in which an attacker targets a company’s supply chain to compromise its products or services. This can be accomplished by inserting malicious code into software or hardware products, altering or replacing legitimate products with malicious ones, or otherwise infiltrating the supply chain.

9. Attacks On Cloud Systems Increase
Cloud-based systems have become increasingly popular in recent years and offer many benefits in terms of scalability and accessibility. However, they also present new opportunities for cybercriminals, increasingly targeting these systems. Attacks on cloud systems have become more common in recent years. Instead of using local servers or personal devices, the cloud uses remote servers hosted on the Internet to store, process, and manage data and applications. Cloud systems are popular because they provide numerous advantages, such as scalability, cost-efficiency, and ease of use. However, they pose unique security challenges because they use shared infrastructure and are accessed via the Internet, making them more vulnerable to cyberattacks.

10. Increase In Attacks On Mobile Devices
Mobile devices, including smartphones and tablets, have become a primary target for cybercriminals. These attacks often involve malware designed to steal sensitive information or disrupt the device’s normal functioning. Attackers may use a variety of tactics to target mobile devices, including malware infections, phishing attacks, and exploits of software or hardware vulnerabilities. Individuals and companies must be aware of the possibility of mobile device assaults and take precautions to protect themselves, such as adopting strong passwords and other security measures, activating two-factor authentication, and keeping their compact software and systems up to date.

11. Cyber Espionage Has Become A Bigger Threat
Cyber espionage involves using cyber attacks to gather sensitive information for political or economic gain. These attacks are becoming more common and can have significant consequences for individuals and organizations. Cyber espionage, often known as cyber spying, uses digital tools and tactics to obtain sensitive information or intellectual property from individuals, corporations, or governments for strategic or malicious reasons. Interception of communication, theft of data from computer systems, or exploitation of vulnerabilities in software or hardware are all examples of cyber espionage.

12. Rise Of Cryptojacking
Cryptojacking is a way of cybercrime in which attackers use malware to hijack a victim’s device and use it to mine cryptocurrency. These attacks can be difficult to detect and can significantly impact the performance of the victim’s device. Cryptojacking is a cyber attack in which a hacker exploits a victim’s computer’s processing power to mine cryptocurrency without the victim’s knowledge or permission. In most cases, this is accomplished by inserting malicious code into a website or software, downloaded and executed on the victim’s machine. The hacker can mine cryptocurrency using the victim’s resources, which can then be sold for a profit.

13. Attacks On Industrial Control Systems (ICS) Increase
Industrial control systems (ICS) control and critical monitor infrastructure, including power plants, water treatment facilities, and transportation systems. TheseIndustrial control systems (ICS) are computer systems that control and monitor industrial processes and infrastructures like power plants, water treatment plants, and manufacturing plants. Because these systems are critical to the operation of many industries, they are frequently targeted by attackers.

14. Increase In Attacks On Financial Institutions
Financial institutions, including banks and credit card companies, are prime targets for cybercriminals. These attacks often involve stealing sensitive financial information or disrupting financial transactions. Attacks on financial institutions can seriously affect individuals and communities because they play an important role in our economy and society. It is critical to follow the law and use legal channels to resolve any concerns or grievances. Suppose you are concerned about the security of your personal financial information. In that case, you may protect yourself by using strong, unique passwords and keeping your computer and other devices up to date with the most recent security patches.

15. The Rise In Social Engineering Attacks
Social engineering attacks involve manipulating individuals into divulging sensitive information or performing actions that compromise their organization’s security. These attacks can take many forms, including phishing scams, pretexting, and baiting. Social engineering attacks are methods of cybercrime that uses psychological manipulation to trick people into disclosing sensitive information or performing actions they would never do otherwise. Phishing emails, pretexting, baiting, and scareware are all examples of such attacks.

16. Attacks On Virtual Currencies And Exchanges
Virtual currencies, such as Bitcoin and Ethereum, have gained significant popularity recently, and cybercriminals are increasingly targeting them. This includes attacks on virtual currency exchanges and scams and fraud involving virtual currencies. This involves gaining unauthorized access to a digital wallet belonging to an exchange or an individual, usually with the intent of stealing funds. Hackers may employ various methods, including phishing scams, malware, or exploiting vulnerabilities in the exchange’s security systems.

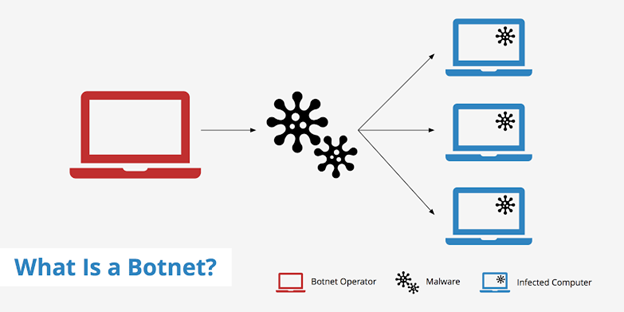
17. Use Of Botnets In Distributed Denial Of Service (Ddos) Attacks
A botnet is a wide network of compromised computers controlled by a single entity. Cybercriminals often use botnets to launch distributed denial of service (DDoS) attacks, which can overwhelm a website or network with traffic and make it inaccessible. A DDoS attack involves using a large number of compromised computers (also known as “zombies”) to flood a website or other online service with traffic to render it unavailable to legitimate users. Using a botnet to carry out the attack, the attacker can produce a high quantity of traffic, making it difficult for the targeted website or service to handle the load and become inaccessible.
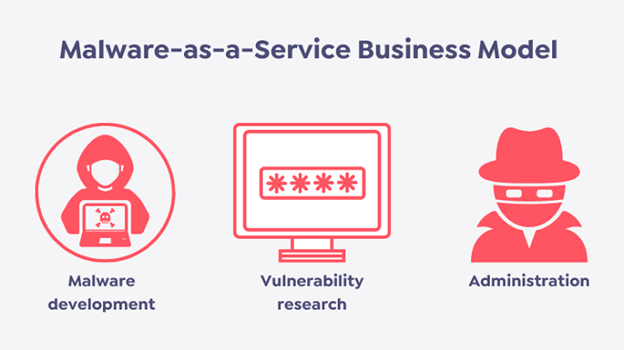
18. Increasing Use Of Malware-As-A-Service (Maas)
Malware-as-a-service (MaaS) is a type of cybercrime in which attackers offer malware-as-a-service to other cybercriminals. This allows even inexperienced attackers to launch sophisticated attacks, as they can purchase and use pre-developed malware. This attack has grown in popularity in recent years because it allows even inexperienced attackers to carry out sophisticated and potentially damaging attacks. Maas attacks can be carried out in a variety of ways. One common method is for attackers to pay a third party for access to a malware toolkit or exploit kit, which they can use to carry out the attack. These toolkits frequently include various malware types, instructions on how to use them, and support from the toolkit’s creators.
19. The Rise In Attacks On Government Agencies
Government agencies are a common target for cybercriminals, which may be seeking to disrupt critical government functions or steal sensitive information. These attacks can have significant consequences for the agency and the general public. The breach of the Office of Personnel Management (OPM) in the United States in 2015 was one example of a high-profile cyber attack on a government agency. Hackers obtain obtained access to the personal information of over 21 million current and former federal employees, including sensitive information such as social security numbers and background check information, as part of this attack.

20. Increasing Use Of Anonymizing Networks
Anonymizing networks, such as the TOR network, allow users to browse the Internet anonymously. While these networks can be used for legitimate purposes, they also provide a degree of anonymity for cybercriminals, making it more difficult for law enforcement to track their activities. Anonymizing networks, also known as anonymous networks or anonymity networks, are designed to protect the privacy and anonymity of their users by routing internet traffic through a series of servers or “hops,” making it difficult to trace the origin of the traffic. Some popular examples of anonymizing networks include The Onion Router (TOR) and the Invisible Internet Project (I2P).