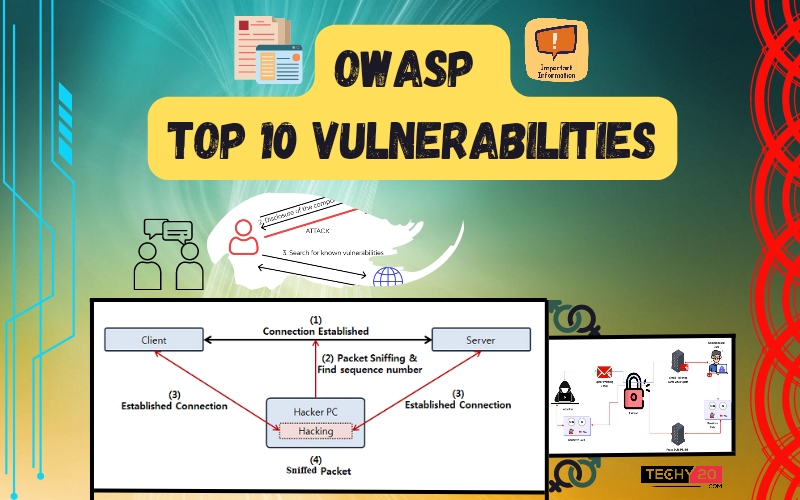
OWASP Top 10 Vulnerabilities
1. Injection If an attacker uses insecure code to introduce their code into a program, this is known as an injection. Because the program cannot

1. Injection If an attacker uses insecure code to introduce their code into a program, this is known as an injection. Because the program cannot

From the time of flip phones (although they are making a comeback) to feature phones, smartphones have advanced significantly. Artists, students, and professionals are now

Several smartphone manufacturers are not bringing or launching their few smartphones, despite the fact that the smartphone industry in India is expanding quickly. Notably, these

In this fast pacing world, technology has become our savior, and as we step further into the future, technology gets adapted as per our needs

The saying goes that the camera you have on you is the best camera. And for the vast majority of us, that means the smartphone

What does “expensive” really mean? So; according to dictionaries, expensive represents anything that costs you a lot of money or sacrifice. And what does expensive
Construction is a significant term in our daily lives. Because it is the basic process of all buildings and industries, we see today. Construction in

Machine learning, neural networks, speech software, and other intelligent problem-solving tools are used by artificial intelligence firms to help organizations. The top AI businesses in

A programming language (a computer language) is the core pillar for game development. Gaming Industry has a revenue of huge amount in today’s world, and

Users of iPhones are likely to mention Apple’s cleaner interface and design, data privacy, security, how easy it is to set up an iPhone right
Businesses utilize the Net Promoter Score (NPS), a widely accepted statistic, to assess customer happiness and loyalty to them. This...
Read moreIn today's fast-paced era, having access to knowledge is crucial for organizations. Effective knowledge management is for organizations of all...
Read moreWebsite optimization tools achieve this goal by helping businesses analyze, improve, and maintain their websites to ensure optimal performance and...
Read moreThe evolution of communication technologies has been a transformative journey, advancing from basic forms of communication to complex and interconnected...
Read moreModes of Communication have changed over the years. The Internet has become the fastest means of communication. The speed and...
Read moreTo have success in SEO strategy, keyword research is the boss. Without good keyword research, ranking high on search engines...
Read more© Copyright 2022-2025 by Techy20. All Rights Reserved.