Linux servers are widely used in applications and services, which makes them a prime target for cyber attackers. It is crucial to prioritize security measures to safeguard your server. Here are 20 techniques for strengthening Linux server security and bolstering its protection.
1. Keep Your System Up To Date
Regularly updating your Linux server is crucial to maintain its security and stability. This proactive approach helps ensure the server remains protected and equipped with the latest safeguards, keeping your data and operations secure.
2. Disable Unnecessary Services
By reducing the number of available attack surfaces, you minimize the risk of exploitation by potential attackers. By regularly reviewing unnecessary services, you can effectively mitigate security risks and strengthen the overall security of your server.

3. Implement Two-Factor Authentication (2FA)
enhance security by requiring a layer of verification, such as a code sent to a user’s smartphone or another trusted device. It significantly reduces the chances of access.

4. Configure Firewall Settings
Optimize your firewall configuration by allowing services and connections, thereby minimizing the attack surface area. It ensures that only legitimate traffic is permitted while keeping threats at bay. A firewall plays a role in protecting your server by filtering incoming traffic. It helps defend against network-based threats like denial-of-service attacks, port scans, or unauthorized access attempts. A well-configured firewall enhances the security posture of your Linux server and plays a crucial role in maintaining the integrity and confidentiality of your network communications.
5. Use SSH Key-Based Authentication
Switching from password-based SSH login to key-based authentication is a highly recommended security practice for your server. Instead, users are required to authenticate using a unique cryptographic key, which enhances the security of your server and protects against unauthorized access attempts. This method provides security measures as it reduces the vulnerability to brute force attacks.
6. Enable System Auditing
Another important step is enabling system auditing. By doing so, you can. Identify any security events or suspicious activities that may occur. It is advisable to review the audit logs to detect threats effectively.
7. Remove Unused Privileged Accounts
By removing privilege-locking accounts and avoiding default system accounts, you can minimize the risk of unauthorized access to your system. It helps prevent damage caused by successful intrusions, protecting your data and operations from compromise and enhancing the overall security of your server. Minimize the potential damage caused by successful intrusions.
8. Protect Files And Directories
Protecting files and directories is also essential. Set file permissions and ownership for these resources, restricting access only to authorized users or groups. It ensures that unauthorized modifications or access are effective.
9. Implement Intrusion Detection Systems (IDS)
Implementing an intrusion detection system (IDS) is highly recommended. It is a vigilant watchdog, continuously monitoring your server for suspicious activities or potential attacks. By providing real-time alerts or automatically taking actions when necessary, an IDS significantly enhances the security of your system by detecting and responding to any security incidents promptly, minimizing the risk of compromise or data breaches.

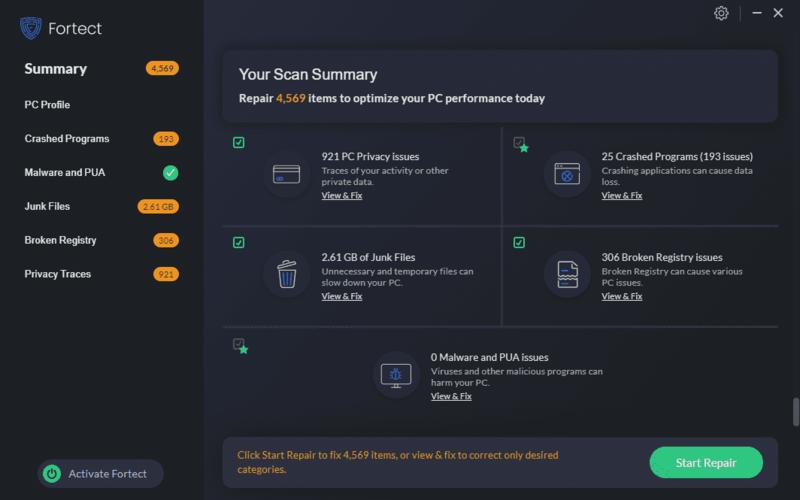
10. Perform Regular Backups And Disaster Recovery Planning
Additionally, regular backups of server data and having a disaster recovery plan in place are steps toward ensuring business continuity. In addition to security measures, regularly backing up server data and creating a comprehensive disaster recovery plan is critical for ensuring business continuity. If your server is compromised, having up-to-date backups enables you to restore data and minimize downtime. A well-defined disaster recovery plan outlines the steps to take in case of an incident, allowing for a prompt and efficient recovery process.
11. Implement Intrusion Detection Systems (IDS)
Finally, consider implementing Security Enhanced Linux (SELinux) or AppArmor, which enforce mandatory access control policies on your system, for security measures. These frameworks offer a level of security by limiting access or activities.
12. Ensure Access
When remotely accessing your server, it secure protocols such as SSH (Secure Shell) or VPN (Virtual Private Network). To maintain the security of your remote access sessions and protect sensitive information, always opt for secure protocols that prioritize data encryption and secure authentication methods.
13. Disable Direct Root
Instead, use an administrative account with sudo privileges. It helps minimize the risk of privilege escalation attacks by preventing access to the root account.
14. Employ Firewall And Intrusion Detection Systems
Employing firewall and intrusion detection systems can enhance security by monitoring network traffic and detecting malicious activities. Regularly updating and patching systems and applications is also essential to address vulnerabilities and stay ahead of potential attackers. Conducting periodic security audits and penetration testing can help identify weaknesses in the system and take necessary preventive measures.
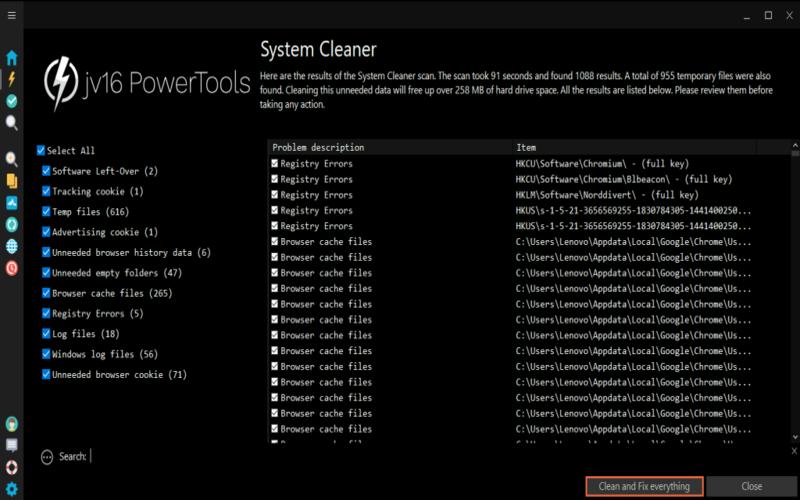
15. Safeguard Web Applications With Web Application Firewalls
Safeguard your web applications running on the server by implementing a web application firewall (WAF). It is important to promptly respond to any alerts or anomalies to mitigate the impact of attacks. By implementing these measures, organizations can protect their web applications from potential threats and ensure the safety of sensitive data.
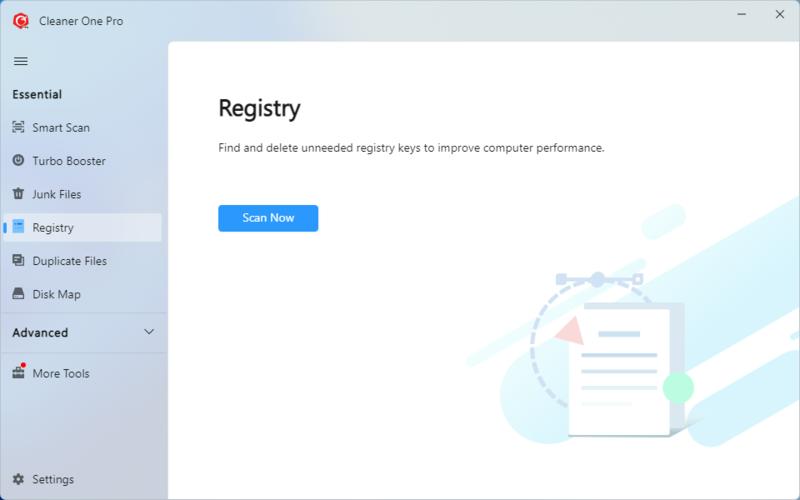
16. Implement Granular Access Controls
Implementing granular access controls and strong password policies can enhance security by reducing the likelihood of unauthorized access. Regularly monitoring network traffic and implementing intrusion detection and prevention systems can help detect and block malicious activities. By taking these proactive measures, organizations can minimize the attack surface and significantly reduce the vulnerabilities on their servers, strengthening their overall security posture.
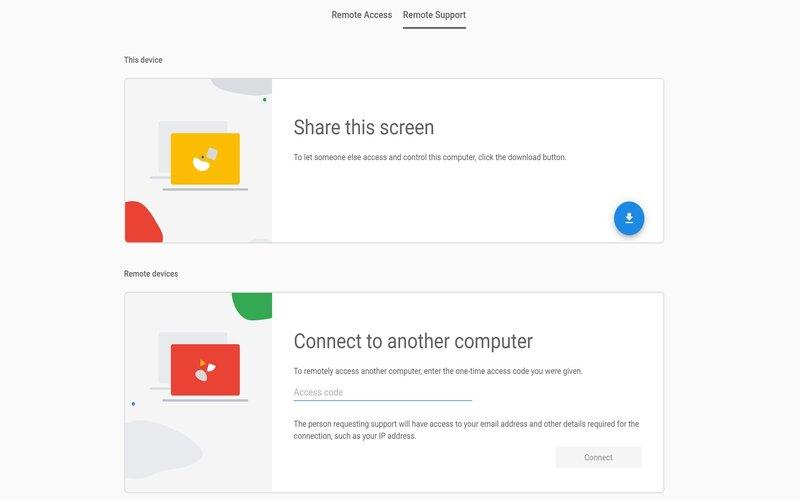
17. Monitor Network Traffic
In addition to file integrity monitoring, implementing strong and regular backup procedures is necessary to protect against data loss or system compromises. By backing up critical files and data, organizations can quickly restore their systems after a security incident. Regular audits and vulnerability scans can help identify any security gaps and ensure measures are in place to address them.
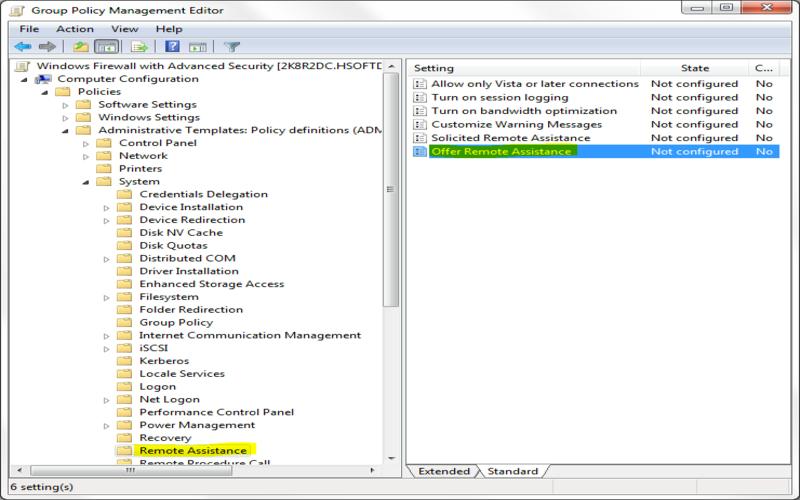
18. Perform Regular Audits
It enables you to proactively address security incidents, reducing the chances of attacks and thwarting potential data breaches. By utilizing tools for monitoring the integrity of files, you can guarantee the continued security and integrity of your Linux server system files.
19. Enable Log Monitoring And Analysis
Proactively identify and respond to potential security threats. Regularly reviewing system logs can provide insights into any patterns of malicious activities. Log monitoring serves as an essential layer of defense, helping organizations maintain the security and integrity of their systems.
20. Implement Secure Shell (SSH) Configuration
Additionally, it’s important to conduct security assessments regularly. These assessments are necessary to ensure that your security measures remain effective. Vulnerability assessments help identify any weaknesses in your server configuration and software, while penetration testing simulates real-world attacks to evaluate the system’s defenses. By addressing vulnerabilities discovered during these assessments, you can promptly implement security measures and reduce the risk of successful attacks and data breaches. Regularly performing security assessments allows you to stay ahead of threats and maintain protection for your Linux server.
Conclusion
Implementing Linux security hardening techniques will undoubtedly strengthen the security of your server. However, it is vital to acknowledge that security is an ongoing process that demands constant monitoring, regular updates, and adaptation to evolving threats. By staying updated, you can remain proactive in implementing the necessary measures to protect your server and stay one step ahead of potential security risks. Regularly reviewing security practices and incorporating new strategies will contribute to maintaining a robust security stance for your Linux server.