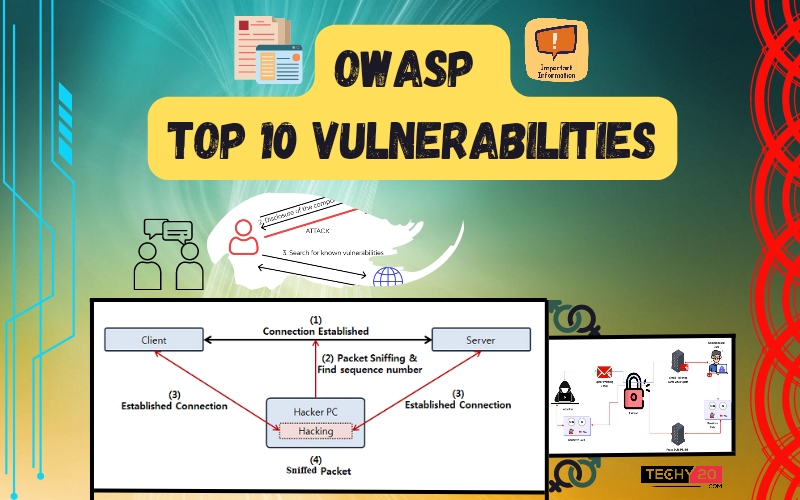
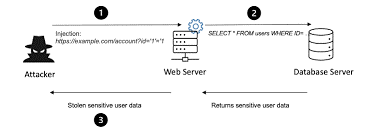
1. Injection
If an attacker uses insecure code to introduce their code into a program, this is known as an injection. Because the program cannot tell the difference between code inserted in this way and its code, attackers can use injection attacks to access specific areas and sensitive data. SQL injections, command injections, CRLF, and LDAP injections are a few examples. Testing for application security can identify injection problems and provide fixes, such as removing special characters from user input or creating parameterized SQL queries.
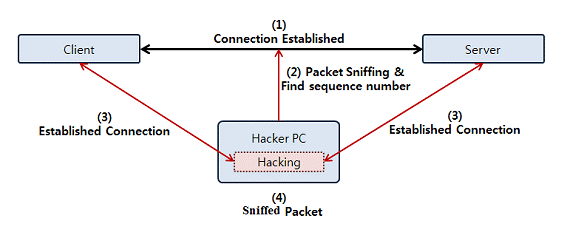
2. Broken Authentication
Calls for authentication and session management that need to be adequately implemented may provide a severe security risk. For example, attackers may find it easy to assume the identity of authorized users because of these weaknesses. Multifactor authentication is one method for avoiding hacked authentication. Before deploying code, use DAST and SCA scans to find and correct implementation problems.
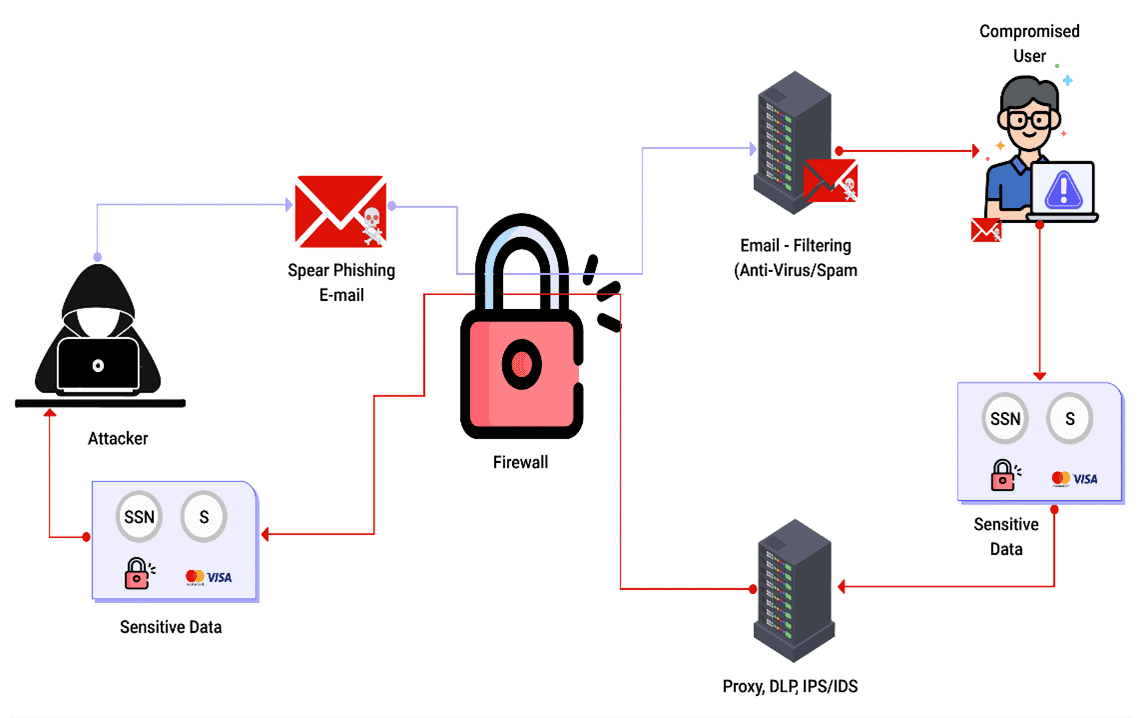
3. Sensitive Data Exposure
Developers can save a tonne of time by using sensitive data exposure APIs, which let them link their program to external services like Google Maps. However, other APIs use risky data transmission techniques, which attackers can use to get usernames, passwords, and other private data. Sensitive data exposure can be minimized by using data encryption, tokenization, sound key management, and disabled response caching.
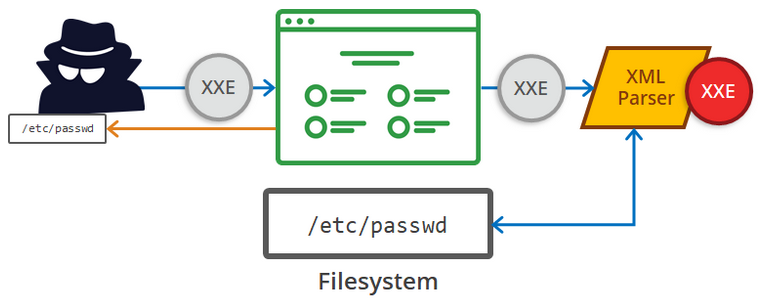
4. XML External Entities
This danger arises when attackers can upload or include malicious XML material due to insecure code, integrations, or dependencies. Third-party components with known vulnerabilities may present hazards, which an SCA scan can detect and alert you to. Additionally, disabling XML external entity processing decreases the likelihood of an XML entity attack.
5. Broken Access Control
Attackers can quickly grab whatever they want if authentication and access restriction need to be correctly established. Unauthenticated or unauthorized users may access sensitive information and systems or even user privilege settings when access control is violated. Since automated systems cannot always test for them, configuration mistakes and unsafe access control procedures can be challenging to spot. For example, although penetration testing can identify missing authentication, different techniques are required to identify configuration issues. With safe coding techniques and preventative steps like locking down administrative accounts and controls and utilizing multifactor authentication, weak access controls and problems with credentials management can be avoided.
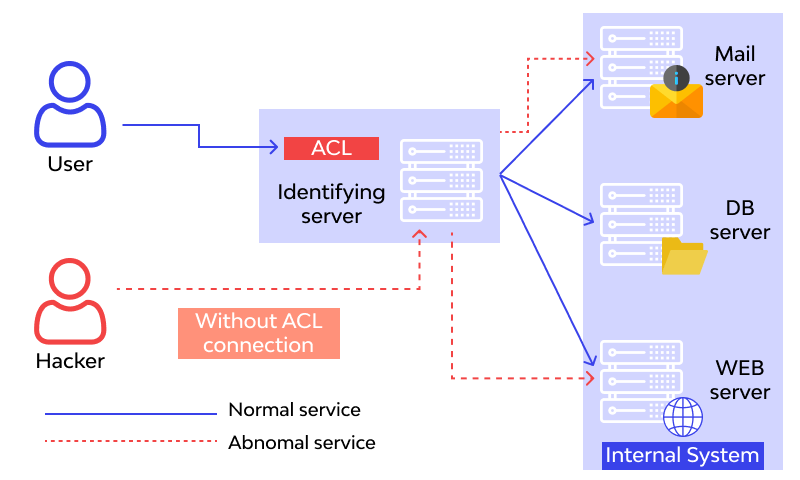
6. Misconfigured Security
More general security configuration errors pose severe risks and make it easy for attackers to access sensitive information and site areas, similar to improperly configured access controls. Using dynamic testing, you can identify poorly configured security in your application.

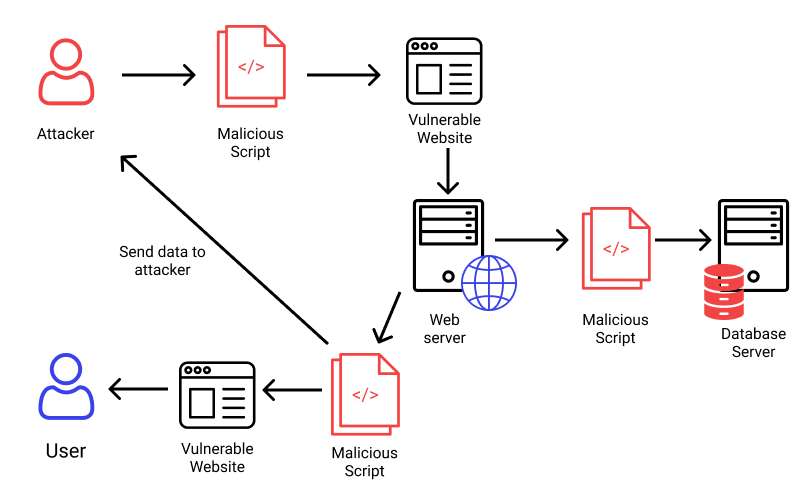
7. Cross-Site Scripting
Attackers can send commands to your application or retrieve data via DOM manipulation and APIs by employing cross-site scripting. Threat actors have a larger attack surface thanks to cross-site scripting, which allows attackers to hijack browsers remotely, go through browser histories, spread Trojans and infections, and more. This risk can be reduced by introducing developers to recommended input validation and data encoding practices. Sanitize your data, for instance, by ensuring that it contains the information you expect for that particular field and encoding it for the “endpoint” as an extra layer of security.
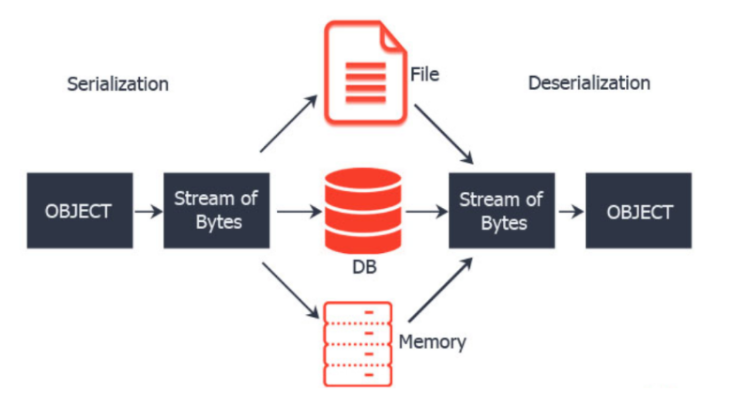
8. Unsecure Deserialization
Deserialization, or the process of reading information and objects saved on discs or another way, can run software remotely in your application or as a gateway for other attacks. For example, popular serialization technologies like JSON and XML convert an object into the structured or binary text as it is serialized. This vulnerability happens when an attacker manipulates a program, launches a denial-of-service (DoS) attack, or executes unanticipated code to alter the application’s behavior. Deserialization is a challenging vulnerability to attack, although penetration testing or application security tools can further minimize the risk. Additionally, avoid using methods that only accept primitive data types and accept serialized objects from unreliable sources.
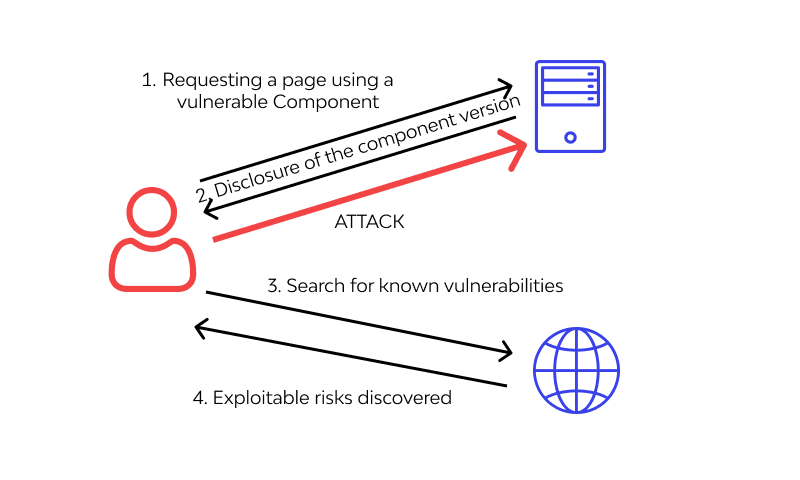
9. Using Components with Known Vulnerabilities
Attackers can use APIs, dependencies, and other third-party components if they are not themselves secure, regardless of your code’s security. You can find and help neutralize vulnerable components in your application using static analysis and software composition analysis. Before publishing an application, developers can use Veracode’s static code analysis tools to discover these complex components.
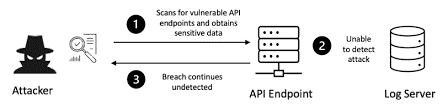
10. Insufficient Logging and Monitoring
Poor monitoring procedures, failure to record problems or assaults, and human error can all increase security concerns. For example, threat actors use a combination of slower remediation times and a lack of monitoring to carry out their attacks before they have a chance to notice or respond. Make sure that any login failures, access control failures, and server-side input validation failures are logged with context so that you can spot suspicious activity in order to avoid problems with insufficient logging and monitoring. Finding portions of your application with insufficient logging is also a significant benefit of penetration testing. Setting up efficient monitoring procedures is also crucial.