A cyber-attack is an attempt to gain access to a computer network or system by cybercriminals, hackers, or other digital enemies, typically with the goal of changing, stealing, destroying, or disclosing information. More than 20 years later, the quantity and severity of cybercrimes have skyrocketed in just a few years due to previously unheard-of occurrences like the COVID-19 epidemic, contested elections, and rising geopolitical upheaval. With time, it is expected that security risks will advance in sophistication and cost more money. While there are many more, this list of cyber-attacks comprises the 20 most typical types of attacks:
1. Spoofing
This is a cyber-attack where the attacker presents itself as a credible source with the intent of doing malicious activities. By engaging with the victim, the attacker tries to get hold of the personal details and eventually demands money or steals data.
2. Ransomware
In ransomware, the victim’s device is detained by the attacker unless the victim agrees to pay a ransom to the attacker. The malware has been designed to take advantage of flaws that neither the system’s creator nor the IT staff has fixed. The target’s workstation is then encrypted by the ransomware.

3. Denial-Of-Service (Dos) Attacks
An intentional, targeted attack known as a denial-of-service (DoS) attack bombards a network with erroneous requests in an effort to interfere with company activities. Users are prevented from carrying out ordinary and essential operations during a DoS attack, such as accessing email, websites, online accounts, or other services run by a compromised machine or network.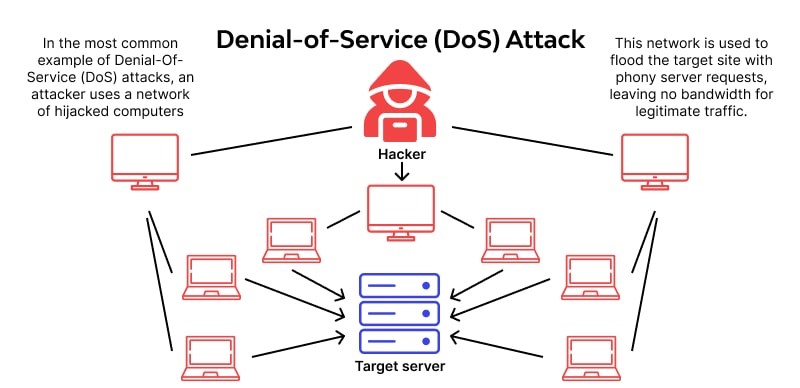
4. Malware
Any program penned with the intention of defacing a computer, network, or server is known as malware, occasionally known as malicious software. The majority of cyberattacks fall under the category of malware, which includes various subtypes like ransomware, trojans, spyware, viruses, worms, keyloggers, bots, crypto jacking, and any other kind of malware assault that makes use of software in an evil way.
5. Man In The Middle Attack
Man in the Middle Attacks is the following on our list of the Top 20 Most Common Cyber Attack Types (MITM). The hijacking of a two-party transaction by hackers is one type of attack. They put themselves in the way of two individuals, computers, or networks and snoop on or modify data exchanged between them. By pretending to be one of the parties, the attacker can make the interaction seem natural.
6. Phishing
Phishing is a type of cyberattack that lures a victim into sharing important information, including passwords or account numbers, or into downloading a malicious file that would infect their computer or phone with viruses using email, SMS, phone, social media, and social engineering techniques.
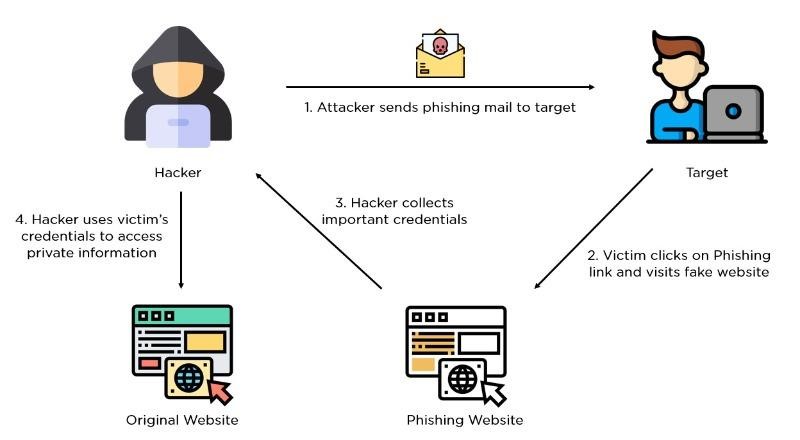
7. Brute Force Attack
In this case, the attacker is merely attempting to guess the login information of a user who has access to the target system. They can then gain access once they guess the correct credentials. Although it may seem tedious and challenging, attackers frequently use bots to crack passwords. A set of credentials that the attacker believes may grant them entry to the secure area is given to the bot. As the bot experiments with the data and finally gets the correct one, access is guaranteed.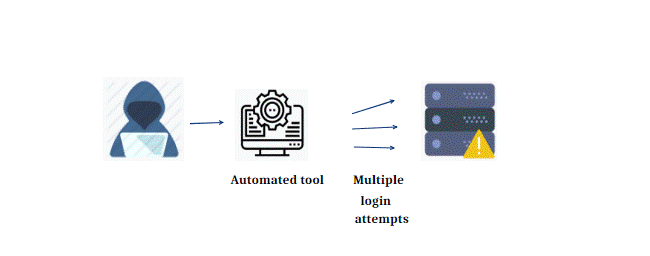
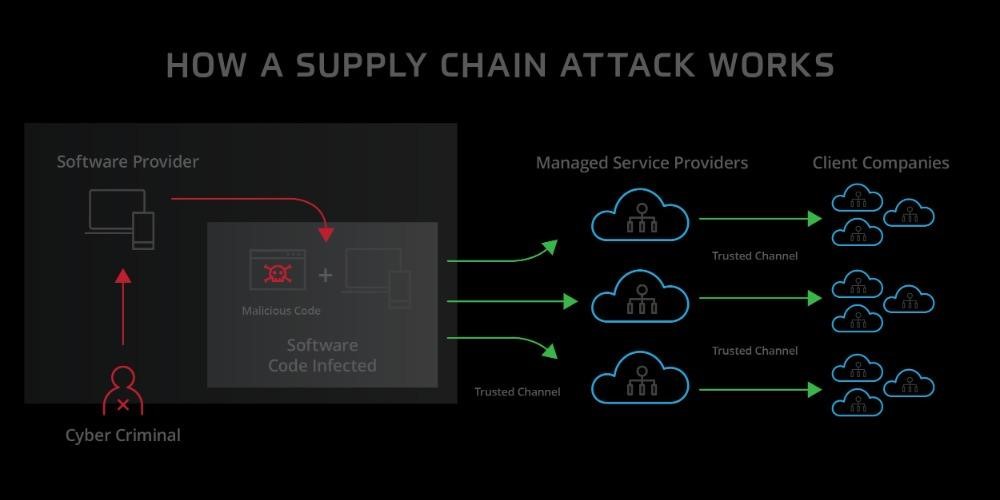
8. Supply Chain Attacks
A supply chain attack is a sort of cyber-attack that targets a reliable third-party provider of goods or services that the supply chain depends on. While in the case of hardware, physical parts of the device are affected by the Supply Chain Attacks, in the case of software attacks, applications are affected.
9. Trojan Horse
A harmful application is cloaked inside a seemingly trustworthy one in a Trojan horse assault. The software inside the Trojan can be used to open a backdoor into the system when the user runs an ostensibly innocent program, allowing hackers to access the computer or network.
10. Identity-Based Attacks
Identity-driven attacks are very challenging to recognize. It is frequently quite complicated to distinguish between a valid user’s regular activity and that of a hacker when a valid user’s credentials have been obtained, and an adversary is posing as that user.
11. Dns Tunnelling
Cyberattacks of the type known as “DNS Tunnelling” use domain name system (DNS) queries and responses to get around more conventional security safeguards and send data and code across networks. After becoming infected, the hacker is free to carry out command-and-control operations. By encoding it in parts in a succession of DNS answers, this tunnel allows the hacker a way to spread malware and/or retrieve data, IP, or other sensitive information.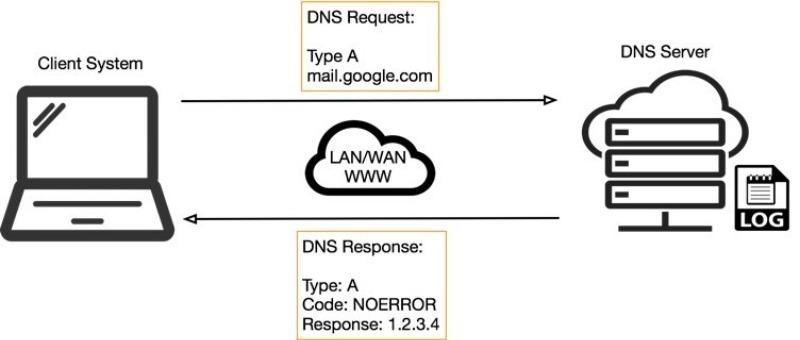
12. Eavesdropping Attack
In these kinds of attacks, the attacker ambushes the network traffic while the same travels through the system. In this way, the malicious party can get hold of private data like bank card details. You can eavesdrop actively or passively.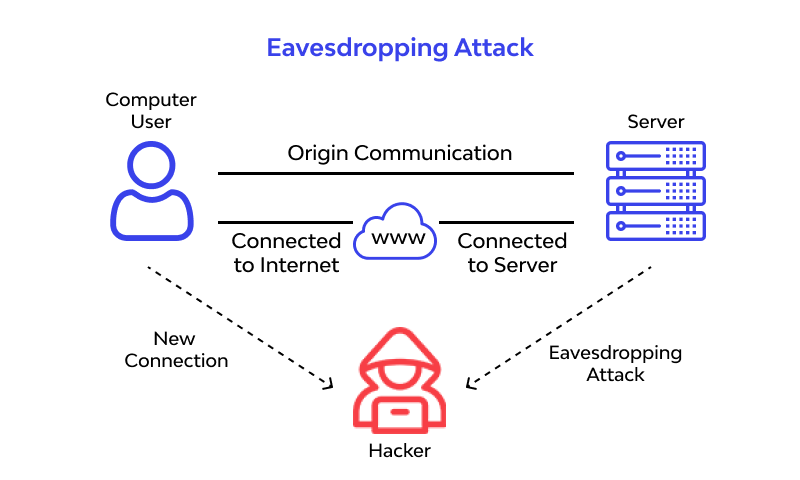
13. Insider Threat
When employees who have authorized access to company technology abuse that privilege to hurt your organization, that is an insider attack. A current user or a former employee with access to the company’s systems can be considered an insider. Insider assaults are highly hazardous and challenging to stop. The attackers are aware of every defense system as well as vulnerable points.
14. Sql Injection Attack
The injection of Structured Query Language (SQL) is a popular technique for exploiting websites that employ databases to serve customers. Clients are computers that access servers for information, and a SQL attack takes advantage of a SQL query sent from the client to a server database. In a data plane, the command is ” injected ” in place of something else that would typically be there, such as a password or login. The command is then executed on the server hosting the database, breaching the system.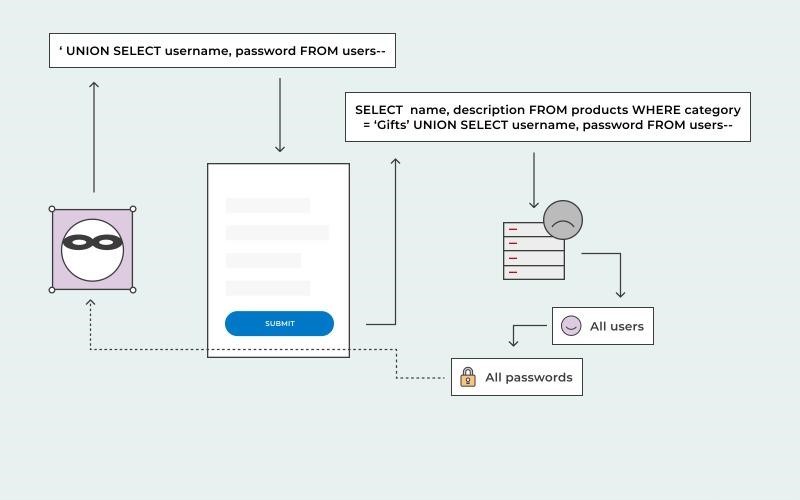
15. Cloud Vulnerabilities
As more businesses switch to cloud delivery methods, the potential of cyberattacks related to the cloud is growing. A wide variety of cyberattacks can be used against cloud services. This includes account theft and Denial of Service (DoS) assaults, which prohibit businesses from accessing their data.
16. Cross-Site Scripting (Xss) Attacks
An attack known as cross-site scripting (XSS) involves injecting malicious code into online applications that are weak. As a result, the malicious code focuses on the content of the website or web application. The malicious scripts are executed by the victim’s browser since it is unable to recognize them. Once they’ve been executed, they have access to all cookies and sensitive data pertaining to the website.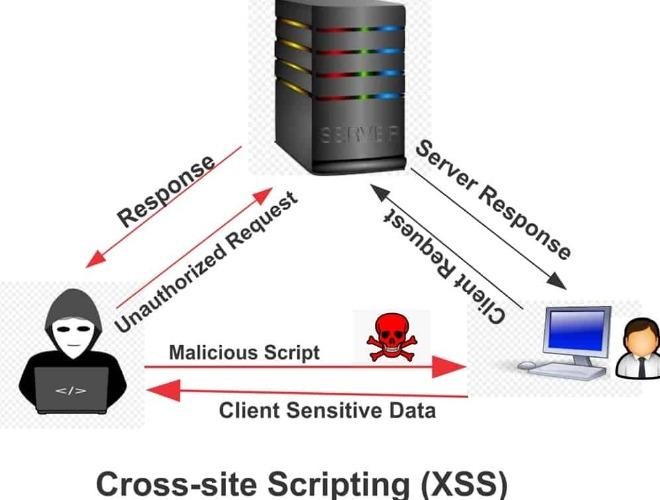
17. Drive-By Attacks
Drive-by Attacks are called drive-by download attacks as well. Another dangerous script triggers an application to download and install itself without consent on a user’s device. Drive-by download attacks frequently happen as users visit and view hacked web pages. Additionally, they use malicious software to find flaws in online browsers, web apps, and hardware.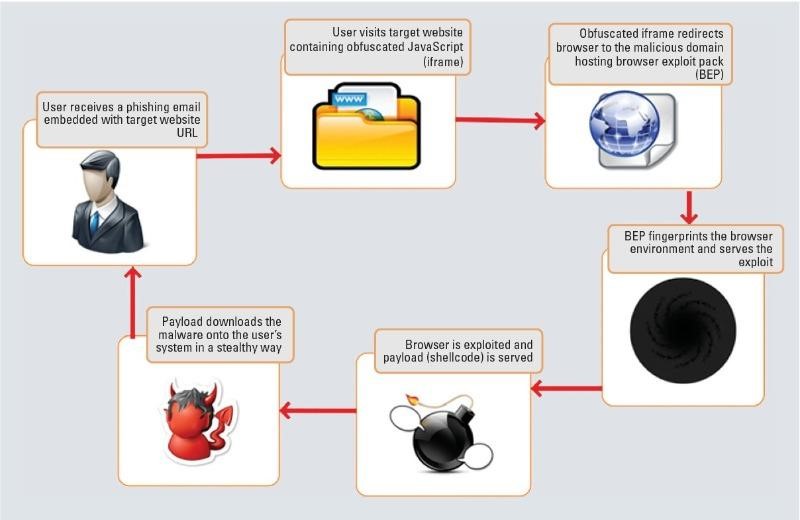
18. Open Ports
When open ports are used by criminal actors to introduce malware or other malicious services or to exploit existing vulnerabilities, they turn into cyber dangers. An early assault method to acquire sensitive corporate data may be a successful port hack.
19. Birthday Attack
Hash methods, which are designed to confirm the validity of messages, are abused by the attacker in a birthday attack. The recipient of the communication verifies the hash algorithm, which functions as a digital signature, before recognising it as genuine. A hacker can simply replace the sender’s message with their own if they can produce a hash that is similar to the one the sender added to their message. Its correct hash will cause the receiving device to accept it.
20. Iot-Based Attacks
Attackers breaking into IoT devices is known as an IoT assault. To steal information, they hack networks and data. The majority of IoT devices lack built-in security features to protect against online threats. They are also primarily created to carry out straightforward tasks, making them extremely open to attacks.