Cryptography is a growing demand for novel, unconventional encryption techniques. It has become a crucial area of study and development as a result of the increased usage of telecommunications technology in recent years, especially when it comes to data transfer securely between two or more different entities when that data is deemed to be critical. The words “cryptography” and “crypto” mean “writing” and “hidden,” respectively. The techniques used in cryptography to protect data are derived from mathematical ideas and a collection of rule-based computations defined as algorithms to transform signals in a way that makes them difficult to decode. Here are a few popular algorithms:
1. AES (Advanced Encryption Standard)
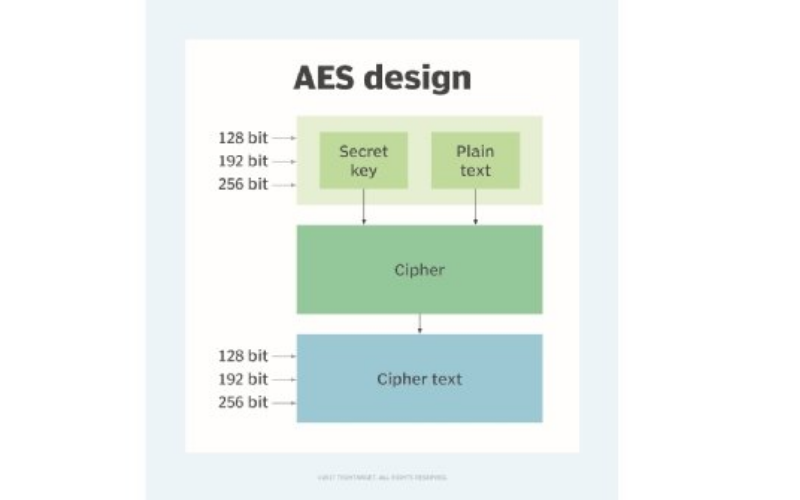
AES is a broadly used symmetric encryption algorithm designed to replace the old Data Encryption Standard (DES). It uses a block cipher with variable key lengths (128-bit, 192-bit, or 256-bit) and operates on fixed-size data blocks. It is considered secure and efficient, making it suitable for several applications, including data protection, secure verbal communication and storage.
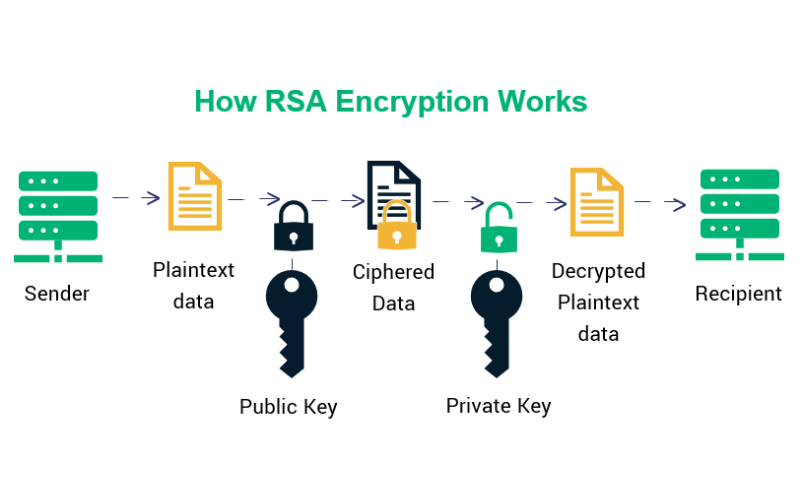
2. RSA (Rivest-Shamir-Adleman)
RSA is a broadly used algorithm for asymmetric encryption named after its inventors, Ron Rivest, Adi Shamir, and Leonard Adleman. It is based on the properties of large prime numbers and includes the usage of public and private key pairs. RSA is commonly used for stable communication, digital signatures, and key exchange. The security of RSA is based on the factorization of huge numbers.
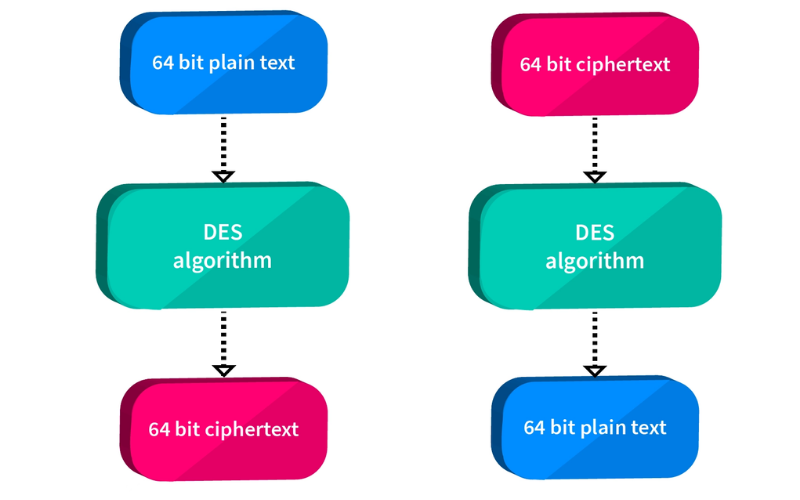
3. DES (Data Encryption Standard)
DES is an older symmetric encryption algorithm from the 1970s. It encrypts and decrypts data in 64-bit blocks using a 56-bit key. It has been widely used for secure communication and data protection, but its key length is too short for modern requirements, making it vulnerable to brute-force attacks. It has largely been replaced through AES.
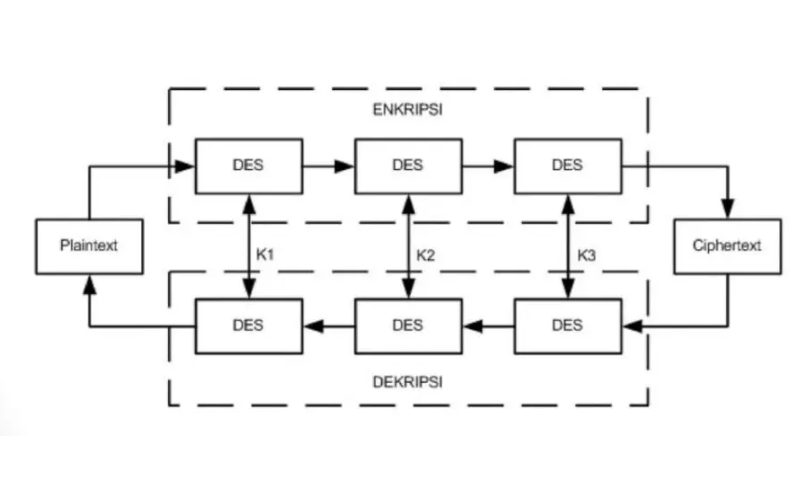
4. 3DES (Triple Data Encryption Standard)
A more sophisticated variant of DES called 3DES employs the DES algorithm three times in quick succession. It uses a 168-bit key derived from 3 56-bit keys. 3DES offers higher protection than DES however is slower in terms of performance. It is used in legacy systems or where backward compatibility is needed.
5. MurmurHash
A non-cryptographic hashing technique called MurmurHash is suitable for use in any hash-based search. The name is derived from the inner loop’s use of the fundamental operations-multiply and rotates. It was written by Austin Appleby in 2008, and both it and its test suite, dubbed “SMHasher,” are currently hosted on GitHub. It also comes in many variations that are in the public domain.
6. RC4 (Rivest Cipher 4)
RC4 is a symmetric encryption algorithm designed by Ron Rivest. It uses variable-length keys and produces a keystream used for decryption or encryption of data. It is used in several applications, including internet security protocols and wireless communication protocols. However, its security has been compromised over the years, and it is not used in new cryptographic systems.
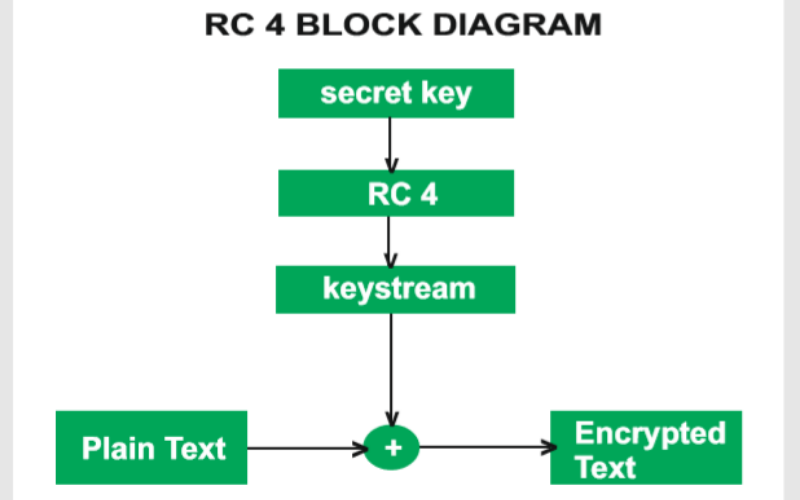
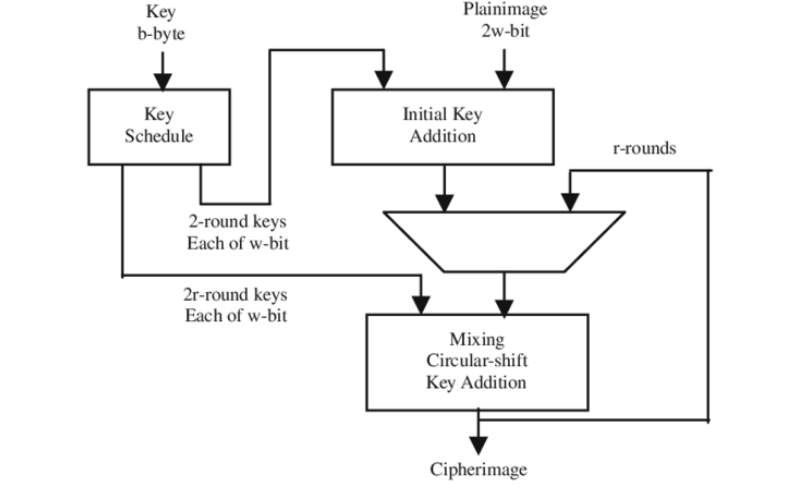
7. RC5 (Rivest Cipher 5)
RC5 is another symmetric block cipher developed by Ron Rivest. It is a parameterized algorithm that supports several encryption rounds, variable block sizes, and key sizes. It is known for its simplicity and flexibility. However, similar to RC4, its usage has declined due to the availability of more secure alternatives and security concerns.
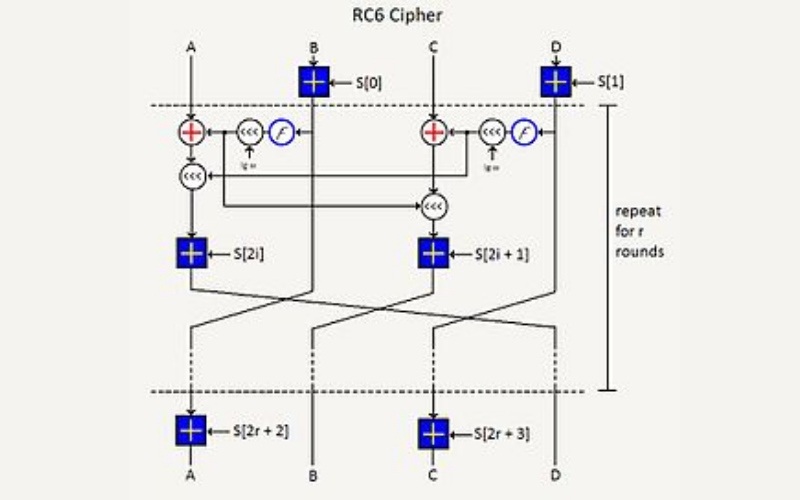
8. RC6 (Rivest Cipher 6)
RC6 is an extension of the RC5 algorithm and was developed by Ron Rivest. It is a symmetric block cipher that operates on variable key sizes and block sizes. It provides a balance between efficiency and security. While it has not gained widespread adoption, it has been included in some cryptographic applications and libraries.
9. ECC (Elliptic Curve Cryptography)
ECC is an asymmetric encryption algorithm based on the mathematical concept of elliptic curves. It offers strong security with relatively short key lengths compared to other asymmetric algorithms such as RSA. It is used in applications where resource-constrained environments or limited computational power are a concern, such as IoT (Internet of Things) devices and mobile devices.
10. SHA-1 (Secure Hash Algorithm 1)
SHA-1 is a cryptographic hash function that generates a fixed-size hash value from input data. It was used for digital signatures and data integrity checks. However, it is no longer regarded as safe for cryptographic applications due to vulnerabilities like collision attacks.
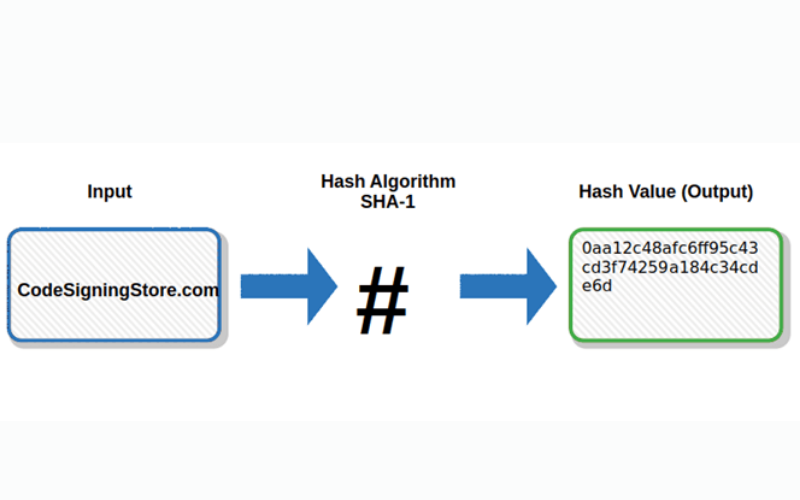
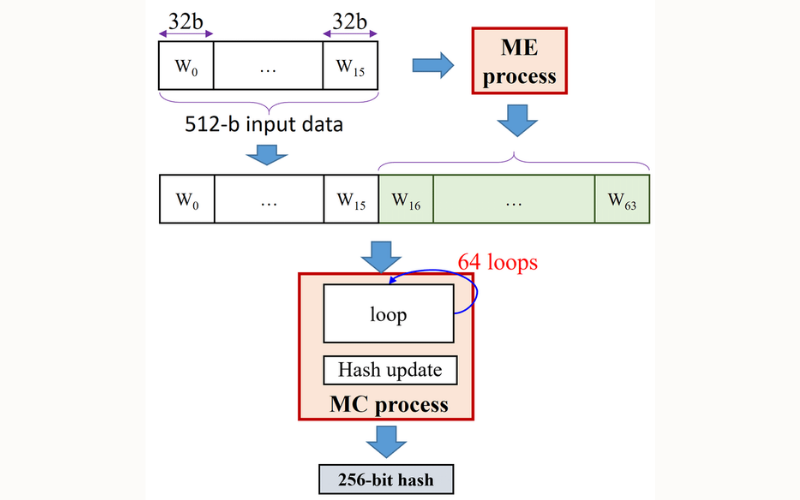
11. SHA-256 (Secure Hash Algorithm 256-bit)
The SHA-2 (Secure Hash Algorithm 2) family of cryptographic hash functions includes the SHA-256 algorithm. It generates a fixed-size 256-bit hash value from input data. It is used for data integrity checks, digital signatures, password hashing, and other security applications. It is considered secure and resistant to cryptographic attacks.
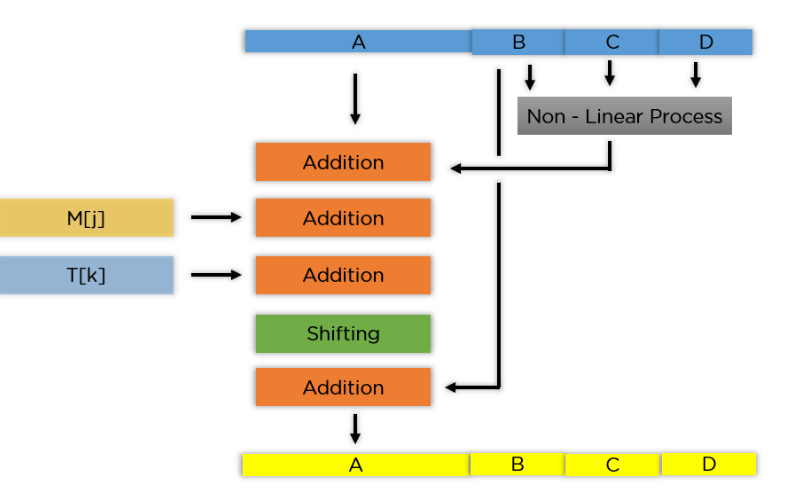
12. MD5 (Message Digest Algorithm 5)
MD5 is a cryptographic hash function that produces a 128-bit hash value from input data. It was commonly used for password hashing, checksums and data integrity. However, MD5 is considered insecure for cryptographic purposes due to vulnerabilities that allow collision attacks.
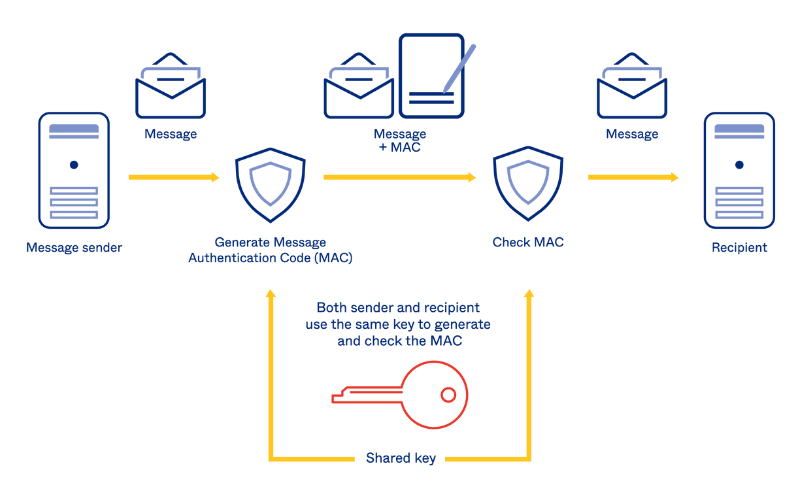
13. HMAC (Hash-based Message Authentication Code)
Message authentication using cryptographic hash functions is done using HMAC. It combines a secret key with the input data using the chosen hash function to generate a hash-based message authentication code. It offers integrity and authenticity of the message, allowing the recipient to verify the integrity of the data and authenticate the sender. HMAC can be used along with several hash functions, including SHA-256 and MD5.
14. DSA (Digital Signature Algorithm)
DSA is a popular digital signature algorithm for verifying and generating digital signatures. It is based on discrete logarithm problems and modular exponentiation. It offers a means for ensuring the integrity, authenticity, and non-repudiation of digital documents and messages. It is commonly used in applications where digital signatures are required, such as digital certificate systems and secure communication protocols.
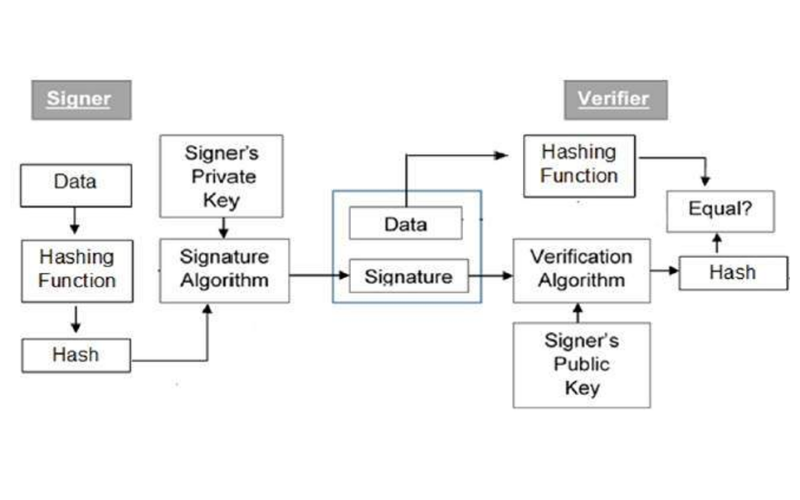
15. ElGamal
ElGamal is a public-key cryptosystem algorithm that offers digital signature and encryption functionalities. It is based on the difficulty of the discrete logarithm problem in a finite field. It allows a sender to encrypt a message using the recipient’s public key, which can only be decrypted using the recipient’s private key. Its digital signatures offer the sender to sign a message using their private key, and the recipient can verify the signature using the sender’s public key.

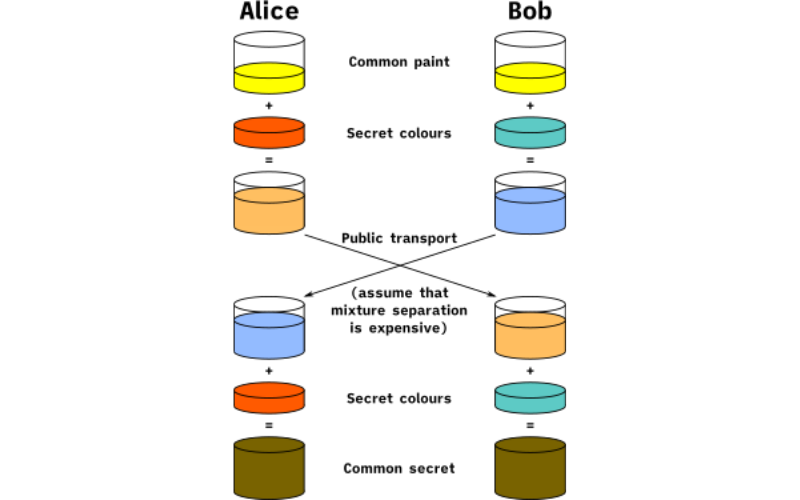
16. Diffie-Hellman
Diffie-Hellman is a key exchange protocol that allows two parties to establish a shared secret over an insecure communication channel. It enables secure communication by allowing the parties to agree on a shared secret without transmitting it directly. It is based on the difficulty of the discrete logarithm problem in a finite field or an elliptic curve.
17. Twofish
Twofish is a symmetric key block cipher that operates on data blocks. It is designed to be secure and efficient and can decrypt and encrypt data using a symmetric key. It is known for its flexibility and can support block sizes of 128 bits and more. It has been widely studied and analyzed for its security properties and is considered a strong encryption algorithm.
18. Serpent
Serpent is a symmetric key block cipher designed to provide a high level of security while maintaining efficiency. Serpent operates on blocks of data and supports various key sizes, including 256 bits, 128 bits and 192 bits. It has several rounds and a complex key schedule, contributing to its strong cryptographic properties.
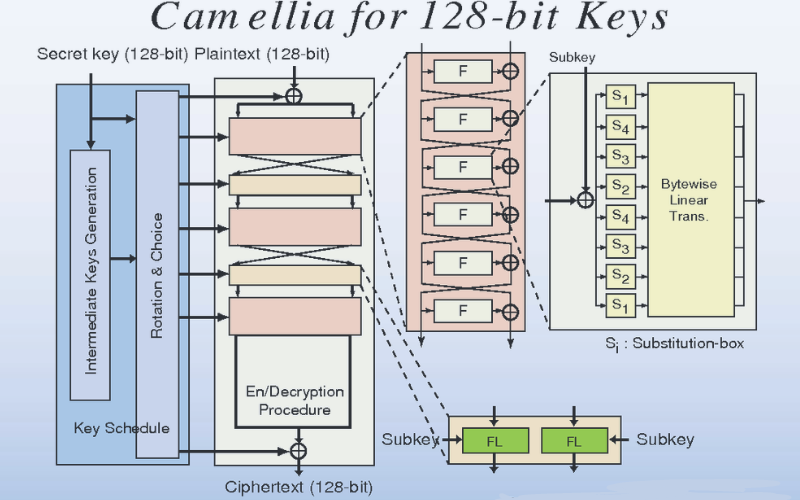
19. Camellia
Camellia is a symmetric key block cipher designed to offer a high level of security and efficiency and has been selected as one of the encryption algorithms for the Japanese government. Camellia supports various block sizes and key sizes, including 192 bits, 128 bits and 256 bits. It offers strong security and has been subject to extensive analysis and evaluation.
20. GOST (Government Standard Cryptographic Algorithm)
GOST is a family of cryptographic algorithms that were developed by the Soviet Union and later adopted by Russia as its national standard. The GOST algorithms include several hash functions, symmetric ciphers and digital signature algorithms. They have been widely used in Russian cryptographic systems and offer a level of security suitable for government and military applications.